Please go to this web page. You can also go to https://portal.wmda.info/ and click on:
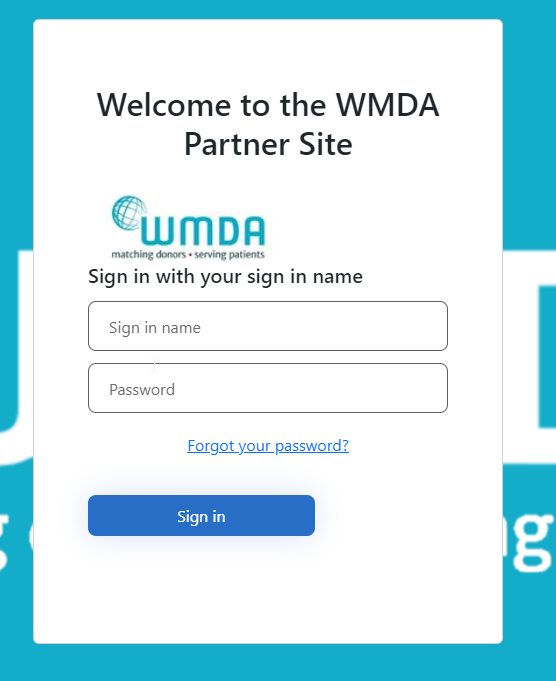
"Login"
followed by
"Forgot your password?"
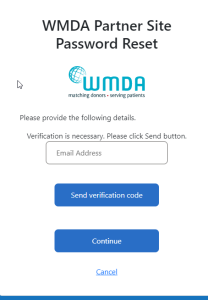
Enter a new password in the upper text box and confirm it in the lower text box
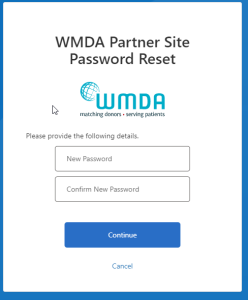
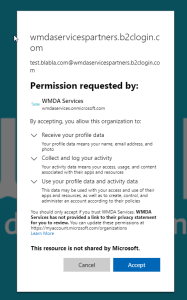
Click Next.
Search & Match Front end
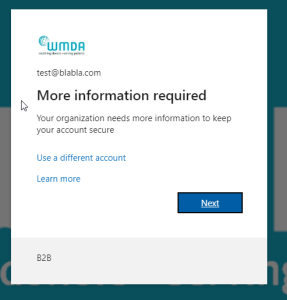
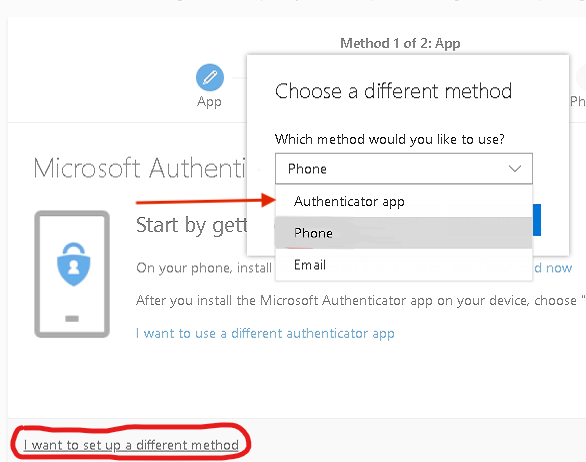
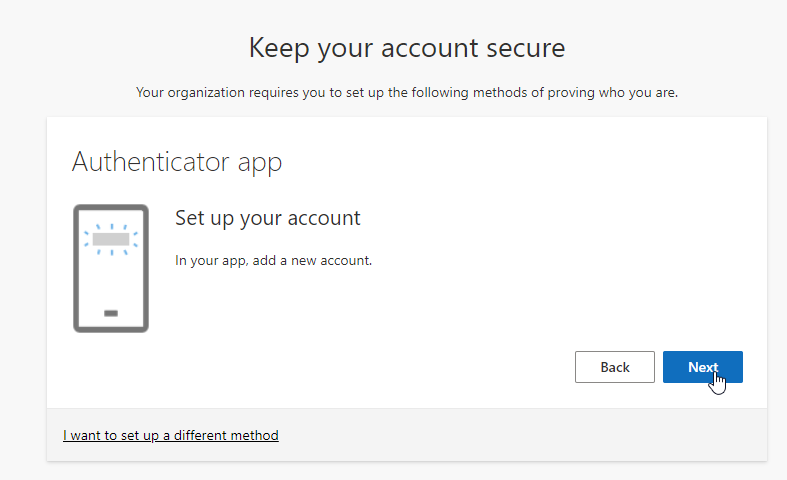
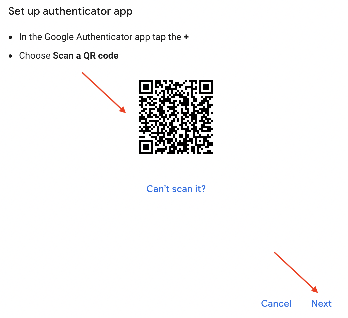
Choose your MFA method. You may choose
- using an authenticator app on your smartphone
- using a hardware token
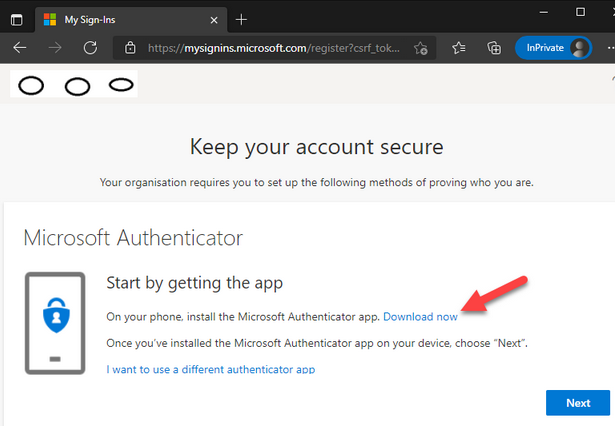
- We recommend Microsoft Authenticator if it is available in your region and on your smartphone/device if you have one. Download (from your smartphone/device) and install it if you don’t already have it. It makes for the easiest MFA login experience.
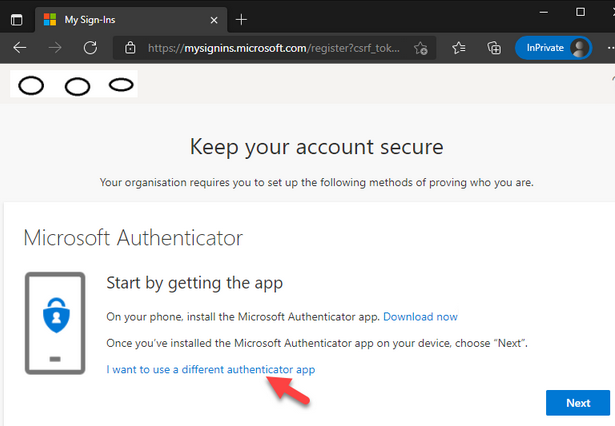
- Alternative MFA tools are Authy or Google Authenticator, and there may be other options in your region
(Please let us know so we can add them to our documentation!) If you are not allowed to use a smartphone you may use
hardware tokens that supports TOTP.
Hardware tokens are devices that work independently from a PC or Phone.We recommend only to use only certified tokens, eg . from https://token2.eu
Tokens should minimally support TOTP, this is a single use six digit code that is uniquely bound to your account and changes every 30 seconds.
Examples of hardware tokens :


Example use : Token2 MoltoThis type of device is programmed once. Once programmed they provide the TOTP code without the use of a PC or mobile phone.
You can program these devices with either a mobile phone that has NFC, or via USB, depending on the model.
Some models allow to store keys for up to 10 different accounts.
There are tokens that need a mobile phone with NFC and an companion app to generate the TOTP code. WMDA does not recommend these tokens. Contact support@wmda.info if you have questions selecting the correct token for your situation.Software token on desktop. There are various desktop applications available for Windows and MAC that provide TOTP tokens. These include:
- Password managers such as Bitwarden, Lastpass and 1Password. In some cases you may need to have a paid subscription. Please check its documentation for instructions on how to set this up.
- Standalone applications such as KeepassXC and Authy. Please check its documentation for instructions on how to set this up.
- SMS is no longer a valid option as Microsoft will soon no longer allow this. Please see Security improvements SMS MFA users WMDA services
Proceed with setting up your second factor method:
|
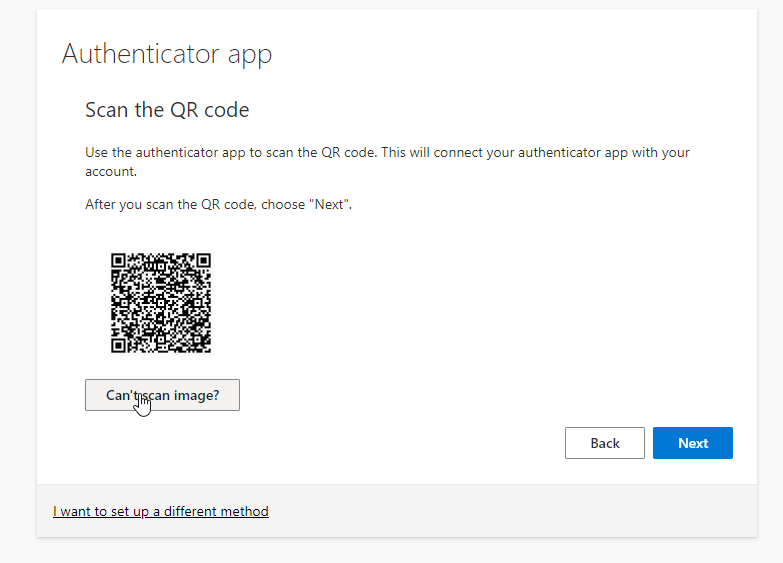
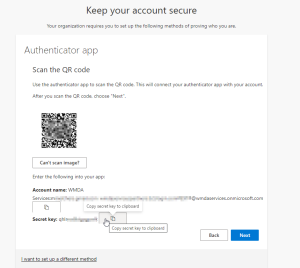
Continue set up:
There are a few more screens to work through, which will vary according to which MFA approach you use.
|
To ensure the MFA was set up correctly, the system will ask the user to verify the the authenticator with a verification code, which is displayed on the next page of the app.
Once all complete, you should be brought back to the original home page, and it should show your email in the top right.

Logging in
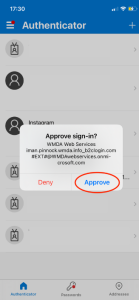
When logging in, after having set up the MFA, the user will be prompted to approve the login, either by entering the code from your authenticator, or tapping the "Approve" pop up in your application (when using Microsoft authenticator)
The Microsoft Authenticator app will show a notification like the one below -