WMDA uses Microsoft login functionality to enable you to login securely with MFA into WMDA web based services. In some cases the following error occurs:
| Code Block | ||
|---|---|---|
| ||
Request Id: 12345678-2e3b-4c96-8e98-e10e6ec52400
Correlation Id: 12345678-0f20-4d51-9012-13e6313806a8
Timestamp: 2022-10-17T09:26:02Z
Message: AADSTS90072: User account 'test.person@testorg.org' from identity provider 'https://sts.windows.net/12345678-abcd-1234-a1b2-123456789abc/' does not exist in tenant 'WMDA Services' and cannot access the application '18373cfc-5469-463f-8793-bd3d30fb9a9b'(WMDA - Search+Match SPA Prod) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account
|
Issue & solution:
You are logged in with your organisation's Microsoft account (in this case test.person@testorg.org) in the same browser as the one you are using for logging into Search & Match or other WMDA services. You are probably using it for services such as Office365/Microsoft365 which include outlook. In order to prevent these issues please use a browser that is not logged into your organisation's office365/microsoft365 account. You can also use incognito/inprivate mode for that.
If the issue persistsBesides the regular B2C login method, there is an alternative way of logging in ("B2B"). It involves using your own organisationown organisation's Microsoft account (in this case test.person@testorg.org) account to login to the WMDA Portal, Search & Match, SPEAR and future other services. Instead of having a separate password for WMDA services, you keep using the password from your own organisation. Your own Microsoft account is "invited" into our environment as a guest. There is just another layer of MFA that is enforced on the WMDA side in order to help secure the applications.
...
After you have accepted the invite and have successfully setup MFA, you are now able to login. The following is different compared to logging in using the normal method:
Information for IT admins at your organisation
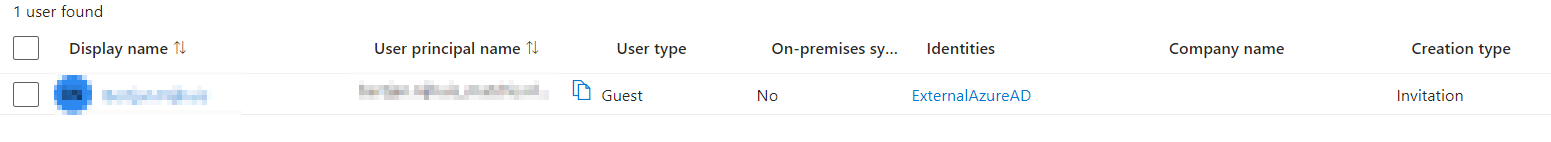
When your organisation uses Microsoft365/Office365 then the Microsoft tenant responsible for WMDA application user authentication (c3ab1869-1472-4577-b669-0d64c732e75c) can invite your users into its tenant. Your organisation's Entra ID may need to allow this connection to work. If permitted AND accepted by the user, your user will be a "guest" in the WMDA tenant and its identity is indicated as from an ExternalAzureAD.
For more information see Microsoft's documentation here: https://learn.microsoft.com/en-us/entra/external-id/what-is-b2b